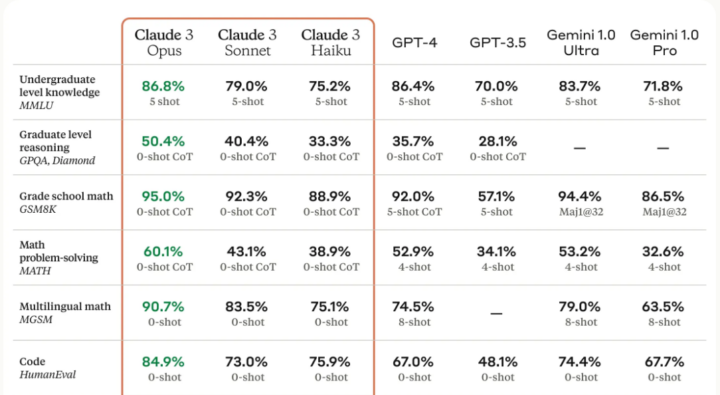
Google has agreed to a settlement over a class-action lawsuit regarding Chrome’s “Incognito” mode, which involves deleting billions of data records of users’ private browsing activities.
The settlement includes maintaining a change to Incognito mode that blocks third-party cookies by default, enhancing privacy for users and reducing the data Google collects.
Profile-guided optimization – The Go Programming Language (golang.org)
Go: The Complete Guide to Profiling Your Code | HackerNoon
Have you already tried Go profiling with PGO?
- More informed compiler optimizations lead to better application performance.
- Profiles from already-optimized binaries can be used, allowing for an iterative lifecycle of continuous improvement.
- Go PGO is designed to be robust to changes between the profiled and current versions of the application.
- Storing profiles in the source repository simplifies the build process and ensures reproducible builds.
https://jvns.ca/blog/2024/02/16/popular-git-config-options/#commit-verbose-true
Here’s a list of useful git options that could be very useful!
https://www.srepath.com/clearing-observability-delusions/
Observability is highlighted as the fundamental practice for all other Site Reliability Engineering (SRE) areas, essential for avoiding “flying blind.”
The article discusses common misconceptions that hinder success in observability, emphasizing the need for the right mindset and avoidance of overly complex solutions.§
The shift towards event-based Service Level Objectives (SLOs) is recommended over time-based metrics, advocating for simplicity and the importance of leadership support in SLO implementation.
https://blog.plerion.com/hacking-terraform-state-privilege-escalation/
The article discusses the security risks associated with Terraform state files in DevOps, particularly when an attacker gains the ability to edit them.
It highlights that while the Terraform state should be secure and only modifiable by the CI/CD pipeline, in reality, an attacker can exploit it to take over the entire infrastructure.
The piece emphasizes the importance of securing both the Terraform files and the state files, as well as implementing measures like state locking and permission configurations to prevent unauthorized access and modifications.
It also explores the potential for attackers to use custom providers to execute malicious code during the Terraform initialization process.
https://thehackernews.com/2024/03/microsoft-confirms-russian-hackers.html
The article details a cybersecurity breach where the Russian hacker group Midnight Blizzard accessed Microsoft’s source code and internal systems.
Microsoft confirmed the breach originated from a password spray attack on a non-production test account without multi-factor authentication.
The attack, which began in November 2023, led to the theft of undisclosed customer secrets communicated via email. Microsoft has contacted affected customers and increased security measures, but the full extent and impact of the breach remain under investigation. The incident highlights the global threat of sophisticated nation-state cyber attacks.